Just Published!
My new post is live: Öffentlicher Zugriff auf Selfhosted Services
Check it out here: https://hierl.dev/posts/oeffentlicher-zugriff-auf-selfhosted-services/
Just Published!
My new post is live: Öffentlicher Zugriff auf Selfhosted Services
Check it out here: https://hierl.dev/posts/oeffentlicher-zugriff-auf-selfhosted-services/
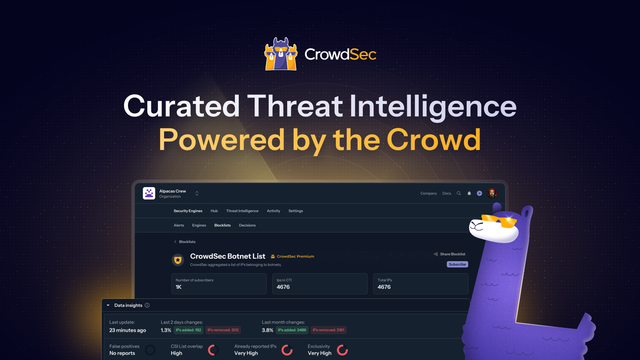
At CrowdSec, we rely on @mongodb to power our solution. Its speed, flexibility, and reliability help us deliver real-time protection at scale, keeping our community safe from evolving cyber threats.
Learn more https://www.mongodb.com/solutions/customer-case-studies/crowdsec

Last chance to share your thoughts! Our CrowdSec WAF & MISP survey closes tomorrow (July 23).
Fill it out, and you might win some special swag — yes, including the alpaca plush!
Survey https://docs.google.com/forms/d/e/1FAIpQLSfJIbHu990Mv1nMjFuirQX0hBjRTrOoo0KaDgrzte3UuO5dgA/viewform
Thanks for helping us make CrowdSec even better!
Sharing insights and taking swift action can collectively reduce the impact of these threats. This is your call to action for real-time threat intelligence and collaborative cybersecurity.
For more information, visit http://crowdsec.net
Want to stay ahead of the latest cyber threats? Get our weekly Threat Alert delivered straight to your inbox, along with critical threat updates and trending cybersecurity insights.
Sign up now for exclusive access: https://contact.crowdsec.net/threat-alert
6/6
How to protect your systems:
Patch: Patch your FortiWeb instance if it is publicly exposed; otherwise, remove outside access to the affected admin panel.
Preemptive blocking: Use Crowdsec CTI to block IPs exploiting CVE-2025-25257
https://app.crowdsec.net/cti?q=cves%3A%22CVE-2025-25257%22&page=1
Stay proactive: Install the Crowdsec Web Application Firewall to stay ahead of exploit attempts, with 100+ virtual patching rules available.
https://doc.crowdsec.net/docs/next/appsec/intro
5/6

Key findings:
A new SQL injection vulnerability in a FortiWeb component allows attackers to execute arbitrary code on the affected machine.
CrowdSec has been tracking exploitation since the 11th of July 2025.
Data from the CrowdSec network indicates that attacker interest in the vulnerability remains very limited.
2/6
Trend analysis:
CrowdSec detected the first in-the-wild exploitation of this vulnerability on July 11th, shortly after we rolled out detection rules. Using our wayback tools, we were able to establish that there were no exploitation attempts before July 11th, confirming once again that public exploits are a key driver of vulnerability weaponization.
For CVE-2025-25257, CrowdSec has observed about 40 distinct IPs producing about 500 attack events in total. Most of these attacks occurred on Friday, July 11th, the day the exploit was publicized. The attacks on Friday were mainly due to a presumably coordinated attacker spinning up a bunch of machines on Scaleway cloud to use in a broad scanning campaign. Over the weekend, the exploit quickly lost popularity. This might be due to the fact that the exploit requires the Fabric Connector administrative interface to be publicly accessible, which is somewhat unlikely. While we cannot make predictions, CrowdSec expects exploitation signals to pick up slightly this week as vulnerability scanners start looking for vulnerable devices. However, we don’t expect the attacker volume for this vulnerability to reach that of other Fortinet-related CVEs.
4/6
About the exploit:
The Fortinet FortiWeb Fabric Connector is an integration component designed to enhance application security by linking FortiWeb web application firewalls (WAFs) with other elements of the Fortinet Security Stack. It enables policy enforcement and automated threat response by leveraging intelligence gathered from FortiGate firewalls, FortiSandbox, FortiAnalyzer, and other “Fabric-enabled” devices. It is in some sense a glue product that holds an array of different Fortinet products together.
The vulnerability allows unauthenticated attackers to execute arbitrary SQL statements against the MySQL database connected to Fabric Connector. As this database runs as root per default, this attack can be chained to run arbitrary Python code on the affected machine, allowing attackers to further compromise the system. The vulnerability affects various FortiWeb versions from 7.0 to 7.6. As a workaround, the vendor recommends disabling the administrative interface to external visitors.
3/6
In this week’s Threat Alert Newsletter: exploitation of CVE-2025-25257 in Fortinet’s FortiWeb Fabric Connector.
We break down how the exploit works, what CrowdSec sees on the network, and steps to stay protected.
Read more
1/6
@Cyberneurones Dans ce même sujet, j’utilise #crowdsec depuis un mois et il me semble pas mal. C'est une manière à grande échelle de partager les IP qui t'attaquent et de profiter de la même information de la communauté.
NGINX Proxy Manager mit CrowdSec absichern - Docker-Setup unter Ubuntu schützen
@kubikpixel @nixCraft Oops.... Too late for my #Crowdsec deployment to my homelab. Hope for the best :-)
This week I learned to deploy #Crowdsec in my #homelab:
- CrowdSec LAPI on an LXC in my private VLAN
- Caddy-bouncer to protect my public servives
- CrowdSec-firewall-bouncer-iptables on my 2 #Proxmox nodes
- CrowdSec agent for all my public VMs and important VMs/LXCs
Of course, I created an #Ansible role to deploy the agent on my multiple hosts/VMs/LXCs using a certificate and a custom port, 8080 is a busy port :-)
Yes, it’s overkill :-)
#infosec #selfhosting #cybersecurity #caddy
Looking to enhance your self-hosted setup with @traefik v3 and CrowdSec for automated threat blocking?
Check out this step-by-step guide by community member Jonny5 covering:
Traefik File Provider (Services/Routers/Middleware)
CrowdSec Remediation Component (for automatic IP blocking)
Parser Agent Config (to detect malicious traffic)
Example Configs for Plex & Web Servers
Full guide https://nova-labs.net/setting-up-traefik-v3-with-file-provider-crowdsec-on-your-homelab/
Community spotlight time: @wazuh and #CrowdSec integration!
We recently shared an Ambassador’s deep dive into the Wazuh-CrowdSec integration and now we’re thrilled to highlight another awesome contributor: Zafer Balkan, who developed the file plugin and helped make this integration a reality.
A huge shoutout to our incredible community members and Ambassadors for making CrowdSec stronger, smarter, and more resilient through their expertise.
Check out Zafer’s tutorial:https://zaferbalkan.com/crowdsec-wazuh-integration/
Soda mit Himbeere. Crowdsec Bouncer Problem behoben.
Anscheinend wollte er meinen schönen neuen API-Key nicht akzeptieren... Dazu musste nur manuell nochmal mit nachdruck darauf hingewiesen werden 
Unser crowdsec-firewall-bouncer läuft jetzt wieder. Sorry für die kurzen Aussetzer. Bitte weiter tooten 
Die #CrowdSec Console ist irgendwie in der Gratis-Version nicht mehr so wirklich sinnvoll für mich, aber ich weiß, dass ich auch irgendwie anders eine grafische Aufbereitung einrichten konnte, ich muss jetzt nur die Anleitung dafür finden.
New CrowdSec Academy course just landed!
Ready to secure your @kubernetes cluster with real-time protection?
Learn how to: Deploy CrowdSec in K8s
Enable TLS
Set up a powerful WAF
Monitor audit logs
Start learning now https://academy.crowdsec.net/course/deploying-crowdsec-in-kubernetes
#CrowdSec #Kubernetes #OpenSource #CyberSecurity #DevSecOps #FOSS @K8sArchitect
My aim for the next day, was to setup a Dashboard for #crowdsec. There is a Web Application hosted by CrowdSec, but they have a limit of 500 Alerts per month. Since many IPs try to brute force my ssh login (I disabled password login, btw), I reach this quota in the first week of a month. Very sad.
So I did some research and figured out, the most generic solution is to use the metric Endpoint, which is compatible with #prometheus I also found an office dashboard from CrowdSec for #grafana!
So my goals were set. I started with Prometheus and collected the metrics (no big deal). Then I got my Grafana up and running and configured the data source for Prometheus. After that imported the Dashboard and I just worked!
Now I got hyped and also added my reverse proxy Traefik to the Prometheus jobs. There was a very up-to-date dashboard for Traefik which I could use. Now I can also display what services are used the most and see more insights of my home lab.
The rest of the day, I used to tweak my dashboards. Now I can see in a Donate Diagram the usage of my services :D See the screenshots below.
3/4