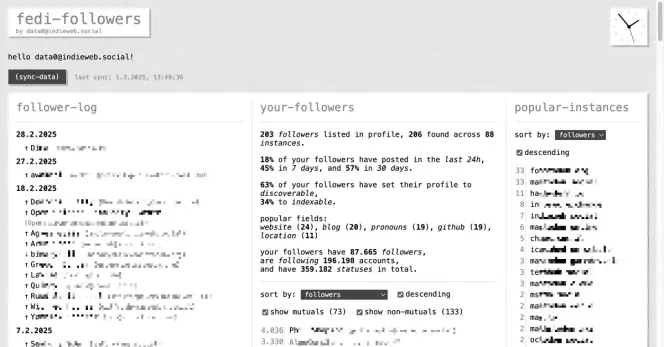
An #E2EE messaging app unaffected by #ChatControl
* App: https://chat.positive-intentions.com/
* Code: https://github.com/positive-intentions/chat
* Reddit: https://www.reddit.com/r/positive_intentions
How it works: https://positive-intentions.com/docs/projects/chat
TLDR: I'm working on a #P2P messaging #webapp. Webapps are generally not considered secure because of the nature of serving statics over the internet. This is correct, but not a limitation of this project. (#selfhosting options: https://positive-intentions.com/blog/docker-ios-android-desktop).
As a webapp, I can provide the app with zero-installation and no-registration. The app is only using (local-only) browser storage (specifically #indexedDB). So in a P2P interaction, the traditional concept of "the cloud" is just the physical devices connected over #WebRTC. This allows for things like P2P authentication: https://positive-intentions.com/blog/security-privacy-authentication.
Future:
I'm aiming to create the most secure messaging app out there... (more than #Signal, #Simplex, #threema, #session, #deltachat, #bitchat, etc). I know I have a long way to go to get there. The UI is fairly ugly for the average user, but I think the mechanics are working as expected. I think #JavaScript is underrated in what you can do with it. I'm actively investigating improving the #encryption approach further to align to how the Signal protocol works (currently using a #DiffieHellman key-exchange).
Support:
In the age of #ChatControl, I would like to keep this project #opensource, but open-source funding is not working for me. I don't want your donations (but don't let that stop you) because it isn't sustainable for a long-term project. I have so far only experienced grant-funding rejections. I have no idea what I'm doing in trying to get funding for this project, so any support/advice is appreciated. In recognition of the project in its current state not being able to get funding... (sorry) I will have to go #closedsource (which I'd like to avoid because it undermines several #cybersecurity claims I'd like to make). I don't accept collaboration on the project because this would make tough decisions like going closed-source also immoral.