#rootkit
Linux rootkits – wykrywanie ukrytych plików i katalogów ( https://nfsec.pl/security/6609 ) #linux #rootkit #detection #twittermigration
Prvé video na našom #youtube kanáli.
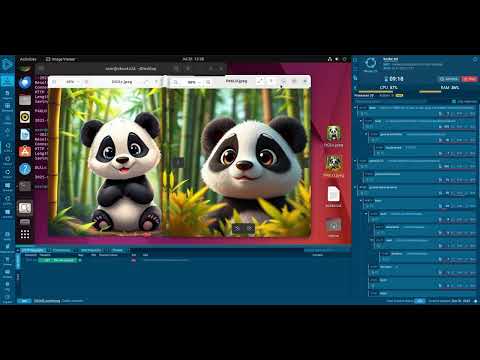
Rýchla analýza malvéru Koske, pri ktorého vytvárani bola použítá umelá inteligencia.
Je to síce "iba" coinminer, teda malvér na ťaženie kryptomien. Má však aj zopár zaujímavostí. Napríklad obsahuje #rootkit, ktorý v systéme skrýva jeho časti.
https://www.youtube.com/watch?v=1OSPp996XQ4
Viac o tomto malvéri si môžete prečíta na https://malwarelab.eu/posts/koske-panda-ai/
It is an AI-generated #Linux #malware which was hidden in images with pandas. It supports wide variety of coinminers for various cryptocurrencies and for GPU and different CPU architectures. Its another component, #rootkit #hideproc, tries to hide the Koske miner from file listings and processes.
https://malwarelab.eu/posts/koske-panda-ai/
Video from #anyrun analysis:
Fake DeepSeek installers are delivering the Sainbox RAT and Hidden rootkit. Our latest blog details how this campaign, attributed to the Silver Fox group, works. #malware #RAT #rootkit #infosec
https://www.netskope.com/blog/deepseek-deception-sainbox-rat-hidden-rootkit-delivery
#Cyber #Security #chinese #deliver #fake #fox #Group #hidden #RAT #Rootkit #Sainbox
Origin | Interest | Match
Netskope Threat Labs has discovered a campaign from the Silver Fox threat actor, using fake installers disguised as legitimate software, including WPS Office, Sogou, and DeepSeek, to deliver the Sainbox RAT and Hidden #rootkit to Chinese-speaker users.
https://www.netskope.com/blog/deepseek-deception-sainbox-rat-hidden-rootkit-delivery
Massiver Cyberangriff auf US-Provider: Erster Einbruch schon ein Jahr früher | heise online https://www.heise.de/news/Massiver-Cyberangriff-auf-US-Provider-Erster-Einbruch-schon-ein-Jahr-frueher-10435438.html #CyberWar #CyberSecurity #Malware #Rootkit #Demodex #SaltTyphoon #GhostEmperor #FamousSparrow #China
https://medium.com/@esrakyhn/kernel-level-rootkit-analysis-and-detection-seeing-the-invisible-0619bb4aaa61?source=rss------technology-5
#rootkit #kernel #linux #technology
Result Details
"#Malware maker sponsors a #shitpost by a #TechIlliterate #Windows n0ob to sell their #Rootkit to #TechIlliterates" would'nt be as clickbaity but a #HonestVideoTitle instead...
Nice how site refers to the application features "monitor employee productivity" back in my day this was called spying using a rootkit.